DNS poisoning is a technique that believes in the DNS server that it has got authentic information when it is not really, in fact. This results in the replacement of false IP addresses at the DNS level, where web addresses are converted into numeric IP addresses.It allows an attacker to change the IP address entries for a targeted site on the DNS server provided with the IP address of server controls. An attacker can create fake DNS entries for the server, which may contain malicious content with the same name.
Rather than being directed to Google's server, as we think, DNS toxicity is used to redirect users to fake pages, which are managed by attackers.
DNS Poisoning
− Exercise
Using this tool, do a practice on DNS toxicity, Ettercap
DNS poisoning is similar to ARP toxicity. To start DNS poisoning, you have to start with ARP toxicity, which we have already discussed in the previous chapter. We will use the DNS spoof plugin which is already present in Itrapp.
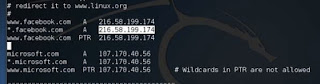
Step 1: Open the terminal and type "nano atter DNS" This file contains all the entries for the DNS address that are used to solve the domain name addresses by the etrepap. In this file, we will add duplicate entries of "Facebook". If someone wants to open a Facebook, then it will be redirected to another website.
Step 2: Now enter the entries under the terms "redirect it to www.linux.org". View
The following example:
Step 3: Save this file now and exit by saving the file. Use "ctrl + x" to save the file
Step 4: After that, the whole process is similar to starting ARP toxicity. After starting ARP toxicity, click "Plugins" in the menu bar and select "dns_spoof" plugin.
Step 5: After activating DNS_spoof, you will see in the results that Facebook will be infiltrated into Google IP by the time someone types it in their browser.
This means that the user gets a Google page on his browser instead of facebook.com.
In this exercise we saw how network traffic could be smuggled through various tools and methods. To provide network security to stop all these attacks, here a company needs a moral hacker. Let's see what a moral hacker DNS can do to stop poisoning.
Defenses
against DNS Poisoning
- As a moral hacker, your work can put you in a state of prevention rather than a pen test. You know that as an attacker you can help you stop the outside techniques.
- Here we are protected against the attack associated with the perspective of a pen tester:
- Use hardware-switched networks for the most sensitive parts of your network, in an effort to isolate traffic in single segments or collision domains.
- To prevent ARP toxicity and spoofing attacks, apply IP DHCP snooping on switches.
- Apply policies to prevent multiple modes on network adapters
- Be careful while deploying wireless access points, knowing that all traffic on the wireless network is subject to sniffing.
- Encrypt your sensitive traffic using encrypting protocols like SSH or IPEC.
- Port security is used by switches, which has the ability to be programmed to only allow specific MAC addresses to send and receive data on each port
- IPv6 has security advantages and options that do not have IPv4.
- Protocols such as FTP and Telnet with SSH have an effective defense against sniffing. If SSH is not a viable solution, consider protecting the old legacy protocol with IPsec.
- Virtual Private Network (VPN) can provide effective defense against sniffing due to their encryption aspect.
- SSL is a great defense with IPsec










No comments:
Post a Comment